Why Passive Recon?
Reconnaissance can be divided into at least two categories, active and passive. Active reconnaissance requires that you interact with the target computer system to gain information about it. Although this can be very useful and accurate, it risks detection. If you're detected doing reconnaissance on a system, the system admin may choose to block your IP address and you'll leave a trail to your subsequent activity.If possible, we would prefer to gather the essential information without ever interacting with the system, thus leaving no trail to trace back to us. That's what passive reconnaissance is.

Step 1Navigate a Browser to Netcraft
Let's open a browser and navigate to the Netcraft website. We should see a webpage that looks like this.
Step 2Search a Domain
As we can see in the screenshot below, We simply typed in a domain and Netcraft returns results for the domain. Notice that in this case, it returned two sites.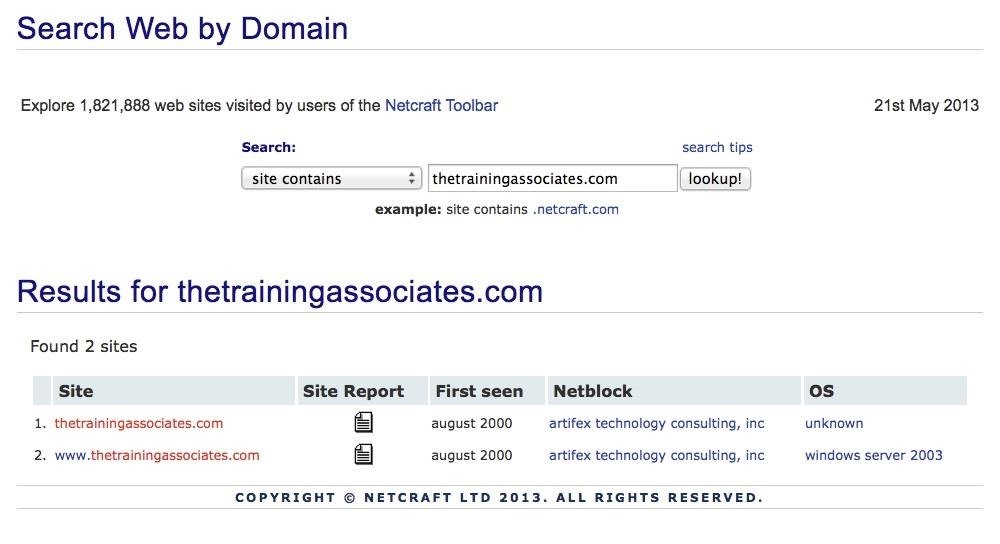
Step 3Open the Site Report
Now we can open the site report and get some critical information about this site. We can see at the top of this report, such information as site rank, primary language, IP address, and nameserver.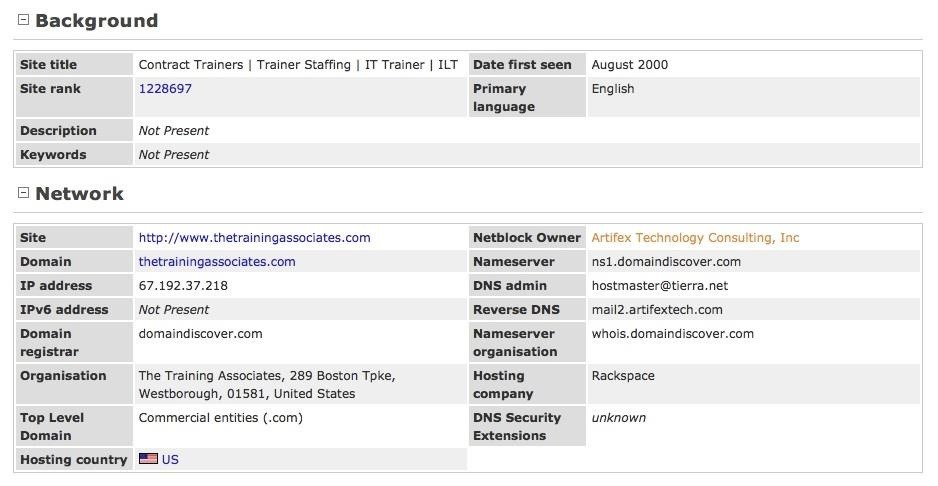
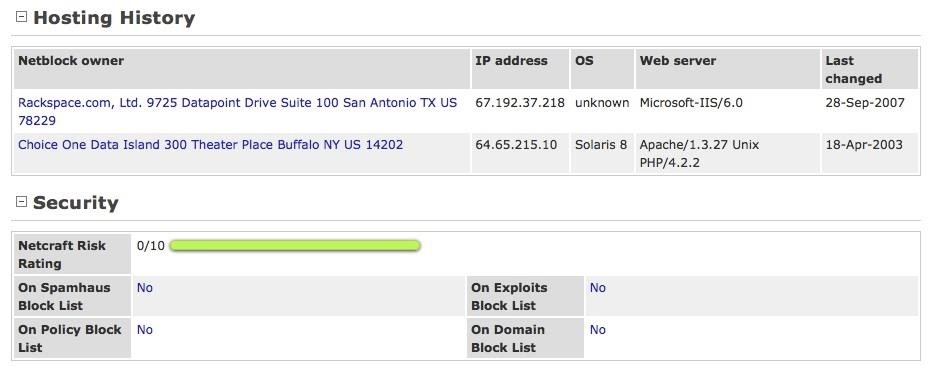
In the case above, we can see it was last updated Sept. 28, 2007. This would imply that any security OS patches that have been supplied in the interim have NOT been applied to this system. As a hacker, this is juicy information as it tells us that any vulnerabilities to this system that have been found since Sept. 28, 2007 are still available on this system as no vulnerability patches have been applied.
Step 4Site Technology
When we scroll down a bit further, we come to a section titled "Site Technology". Here we get a rundown on the technology the site's running.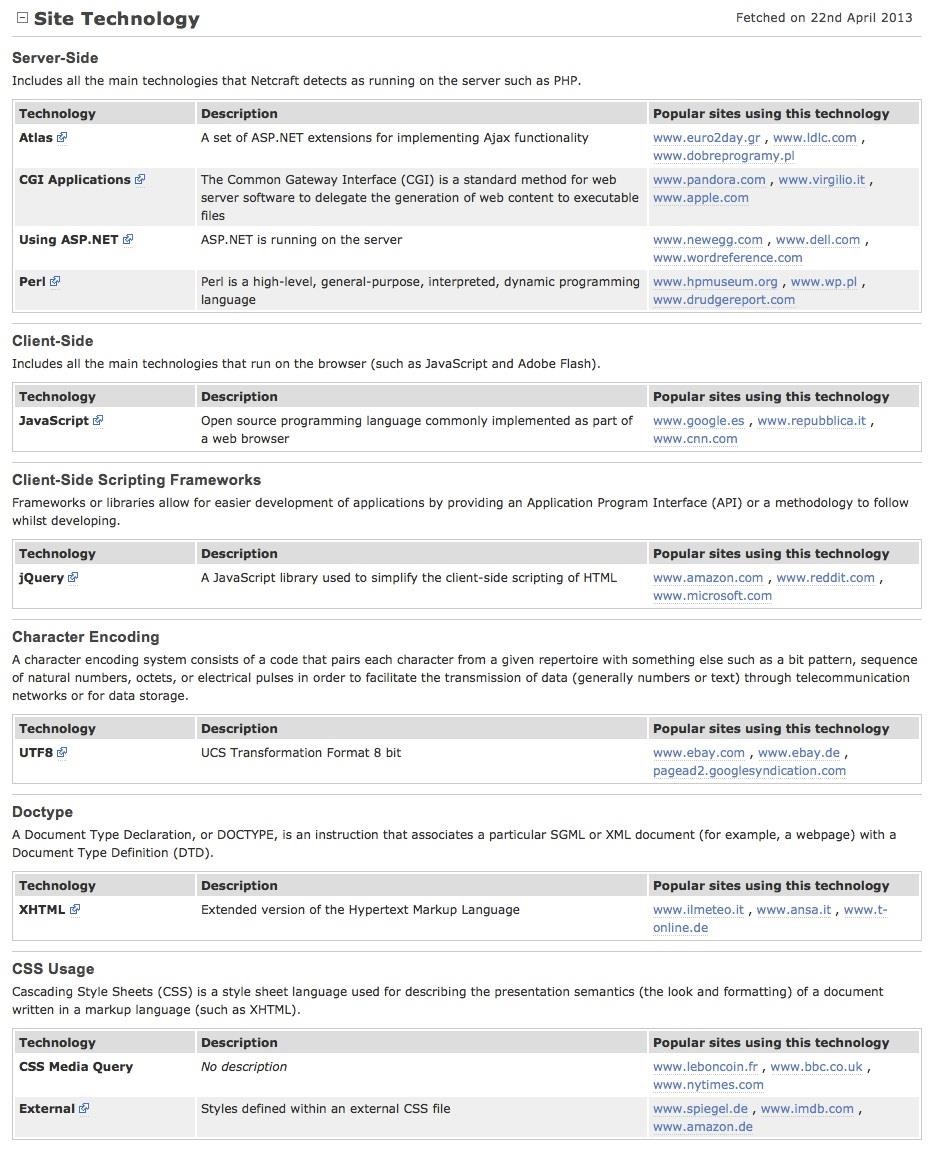
It's important to note here that Netcraft data is not foolproof. I would give it an 80-85% probability of being correct, and that's high enough to garner valuable recon info on a website.