 | |
| nmap banner grabing |
 |
| define |
 | |
| other tool |
Welcome back, my greenhorn hackers!
For over 15 years, a tiny but powerful tool has been used by hackers for a wide-range of activities. This tool goes by the name of netcat, and although well known in hacking circles, it's virtually unknown outside. It's so powerful and useful, that many people within the hacking community refer to it as the "Swiss Army knife of hacking tools."
In this tutorial, we'll look at the capabilities of this simple tool and how the aspiring hacker can use it.
What Is Netcat, Really?
Netcat—like so many hacker tools—was created to be a network analysis tool. Developed by a fellow only known as "Hobbit," he gave away this tool to the IT community without compensation, but has received scores of accolades. Thanks, Hobbit!As such, you can use it to open up TCP and UDP connections between two machines over any port your heart desires. It can also be used as a port scanning tool, similar to nmap. In addition, it can be used for port forwarding, proxying, simple web server, and leaving an open backdoor for the hacker.
Step 1Open Netcat
Once we've fired up our kali linux system and opened a terminal, we can use netcat from any directory since it's located in our bin directory which is in our PATH variable, by default. So, let's type:
- nc -h
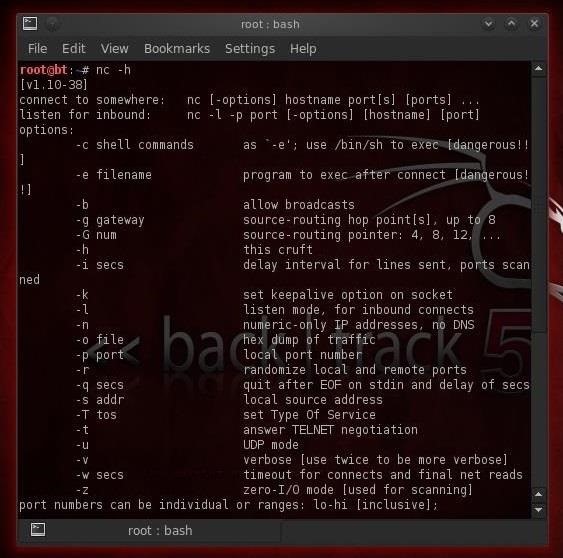
To listen for inbound connections:
- nc options host IP address port
- nc -l -p port
Step 2Use Netcat to Connect to a Remote System
root@rockstardevil:~# nmap www.cnn.com
Starting Nmap 7.40 ( https://nmap.org ) at 2017-04-15 04:38 IST
Nmap scan report for www.cnn.com (151.101.121.67)
Host is up (0.076s latency).
Other addresses for www.cnn.com (not scanned): 2a04:4e42:1d::323
Not shown: 995 filtered ports
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
443/tcp open https
554/tcp open rtsp
1723/tcp open pptp
we get ip here 151.101.121.67 now use this in next steps but i am using another ip
first you have to find latest ip of that website it can be done with nmap exampe on www.cnn.com
Let's use netcat to connect to a remote system. In this case, we will try to connect to a web server on port 80. We type:
- nc 192.168.1.105 80
Step 3Use Netcat to Banner Grab for OS Fingerprinting
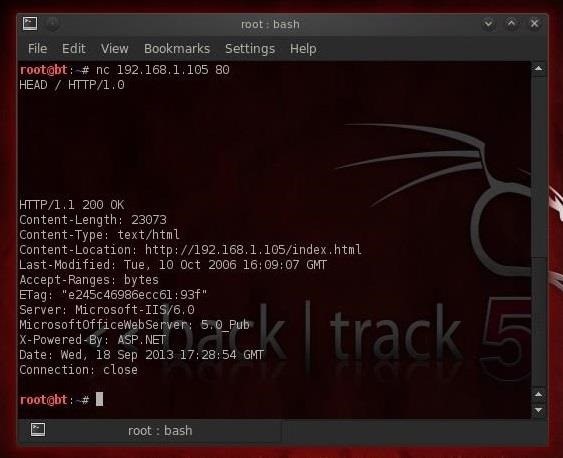
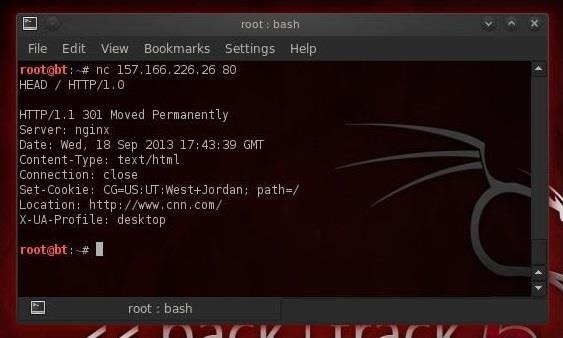
Once we have a TCP connection to a web server, we can use netcat to grab the banner of the web server to identify what web serving software the victim is running.Remember that before attacking any system, we need to know as much as possible about the victim. Netcat can help us with that task by grabbing the banners that web servers serve up to new connections.
- HEAD / HTTP/1.0
- nc 98.129.110.26 80
- HEAD / HTTP/1.0
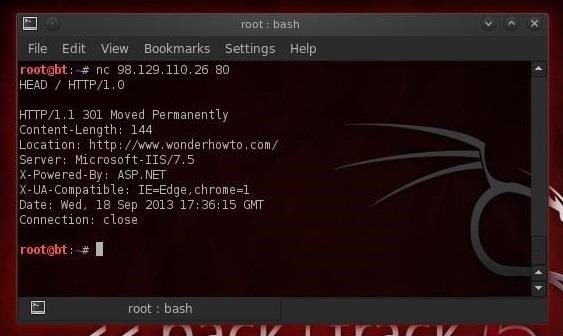
If we try the same thing with cnn.com, we get the results below.
Step 4Use Netcat to Listen for Connections
Now, let's use netcat to create a listener on the remote system. Let's assume that we have a Windows server that we have installed netcat on. We can now type the following to open a netcat listener on port 6996 (it can be any port) on that system.- nc - l -p 6996



